Zscaler ZPA changes how people connect to private apps by quietly reshaping user behavior: instead of “logging into the network,” users just open an app, and the platform decides—based on identity, posture, and risk—whether that moment is safe enough to allow a connection. This article walks through how it works, how the connection is built in both directions, and what it means for human behavior and security culture.
Human behavior and zero trust
Traditional VPN thinking trains users to believe “if the tunnel is up, I’m trusted everywhere,” which encourages risky habits like leaving VPNs always on or reusing access from unmanaged devices. ZPA replaces that with app‑level access, so users never see a flat network and never get a feeling of “once inside, I can go anywhere.”
Because access is driven by identity and posture, people start to associate trust with their current behavior—patching devices, avoiding malicious sites, and following policy—rather than just knowing a password or owning a laptop. This subtly nudges behavior toward continuous hygiene, since risky actions now have direct, visible consequences in the form of reduced access.
How it works (high level)
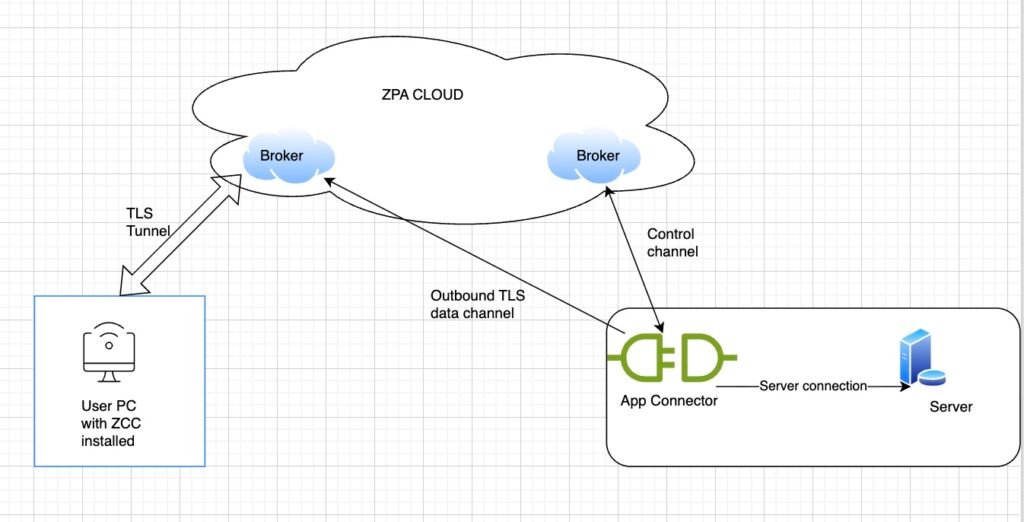
At a simple level, ZPA brokers a private, outbound TLS connection between a user and a specific internal app, without ever placing the user on the internal network. Instead of exposing IPs or opening inbound ports, applications sit behind App Connectors that only establish outbound connections to the ZPA cloud.
The Zscaler cloud—part of the Zero Trust Exchange—acts as a policy brain and meeting point: it authenticates users, checks device posture and risk, and then decides whether to stitch together user and app via a short‑lived, encrypted path. This design removes the “permanent tunnel” mindset and replaces it with just‑in‑time, one‑to‑one access for each session.
How the connection works
- User device and ZPA client
A user on a laptop or mobile device runs a lightweight ZPA client that intercepts traffic destined for private applications, based on defined app segments or domains. The user doesn’t choose networks or tunnels; they simply open the app or URL, which keeps behavior focused on work instead of network plumbing.
- Secure connection to the ZPA cloud broker (TLS, bidirectional)
When the user reaches for an internal app, the client establishes a mutually authenticated TLS session to the nearest ZPA broker in the cloud. This connection is bidirectional, carrying both requests and responses, but it never exposes the internal network—only specific app destinations defined by policy.
At this stage, the broker evaluates identity (IdP attributes), device posture, and dynamic user risk signals, such as recent malicious browsing or DLP violations, to decide whether to allow or adapt access. Human behavior—like clicking risky links—directly influences this risk score, meaning unsafe actions can shrink access in real time.
- App Connector near the private servers
On the app side, you deploy one or more App Connectors in the data center or cloud VPC where private servers live; these are small virtual appliances with no inbound listening ports. Each App Connector maintains its own outbound TLS control channel to the ZPA cloud, registering which application segments it can reach and receiving policy updates.
Because these connectors only dial out, administrators avoid the dangerous behavior of opening firewall holes or publishing internal IPs, which historically trained teams to favor convenience over segmentation.
- Outbound TLS tunnel between broker and App Connector
When policy allows a user to reach an app, the ZPA cloud logically stitches user and app together by selecting an appropriate App Connector and building an outbound TLS tunnel between broker and connector. This is not a route into the network but a narrow, per‑app path: the connector can talk only to defined internal services, and the user can only reach that app, not the surrounding subnet.
The result is a one‑to‑one, user‑to‑app connection:
user PC ⇄ TLS ⇄ ZPA broker ⇄ outbound TLS ⇄ App Connector ⇄ private server.
At no point does the user see internal IP ranges or gain ability to scan or pivot, changing attacker and insider behavior by removing the opportunity for lateral movement.
- Ongoing monitoring and adaptive behavior
During the session, ZPA continuously evaluates user risk and device posture, updating scores based on observed behavior such as malware blocks, C2 traffic, or suspicious access patterns. If the user’s risk rises—for example, interacting with known malicious content—the platform can automatically terminate existing sessions or tighten policies for that individual without impacting others.
This adaptive enforcement sends a clear behavioral signal: risky actions have immediate, personal consequences, encouraging users to self‑correct rather than rely on static, once‑per‑login checks.
Why this changes user and admin behavior
For end users, ZPA removes the friction of choosing gateways, toggling VPNs, and wondering which subnet they’re on, which reduces the temptation to use unsafe workarounds like personal email or shadow IT. Access simply follows identity, device health, and context, so people can focus on tasks while still experiencing the impact of their choices through adaptive access.
For administrators, the shift from network‑centric to app‑centric thinking breaks the habit of over‑provisioning broad access “just in case,” and replaces it with fine‑grained rules tied to groups, posture, and risk. Since access is logged at user and app level, security teams can see who touched what, when, and under what risk level, turning abstract “human risk” into something measurable and actionable.
Conclusion
Zscaler Private Access changes more than the plumbing of remote access; it rewires the behavior around trust by treating every connection as a decision, not a permanent tunnel. Users experience seamless, app‑level access that quietly rewards safe habits and penalizes risky ones, while administrators gain control that is precise, adaptive, and deeply tied to identity and behavior signals.
By moving from “I’m on the network, therefore I’m trusted” to “my current behavior and posture earn just‑enough access to one app at a time,” organizations shrink their attack surface and build a healthier security culture at the same time.